Ransomware: Sweden’s Miljödata hack shows the need to be always vigilant

Ransomware is a major topic of conversation for us at SpaceTime. We live for it. Well, we live to prevent it, or at least to minimize the cost if and when it does happen.
We have written about ways to protect your business against ransomware, but we all just got a timely reminder of exactly what is at stake.
Swedish IT firm Miljödata, which provides digital HR services widely used by the national government, had its systems hacked into by intruders at the end of August. The attackers are believed to have gained access to data belonging to 200 of Sweden’s municipal governments.
Following the attack, the data was published on the dark web. It’s believed that as many as 1.5 million people may be affected.
What exactly happened in Miljödata's case?
Attackers gained unauthorised access to Miljödata’s servers around 22 August. Its systems went dark over the weekend, before coming back online after a ransom of 1.5 bitcoin (roughly $168,000) was paid.
Miljödata has data from its customers (and former customers) on file. The hackers were able to access portions of the data, which has now been made available on the dark web.
Estimates suggested that at least one million people’s data leaked out, but some estimates put the number as high as 1.5 million.
The data is said to include existing clients, hundreds of local government systems, private companies and even some companies that stopped using Miljödata systems some time ago.
The types of data leaked out include personal identity numbers, names, phone numbers, home addresses, email addresses, employee IDs and some sick leave or rehabilitation-case information.
The leak is troubling as, placed in the wrong hands, this data can be used to enable identity fraud, theft, phishing and other malicious activities.

Image: SVT Nyheter
What is next for Miljödata?
It is tough to track the individuals whose data has been compromised, but the government is advising Swedish people to be vigilant and aware of potential contact through SMS, email, calls and more.
The Swedish Data Protection Authority (IMY) is investigating the incident. Depending on its findings, Miljödata may face sanctions. Companies which had data leaked may also face fines around failing to control their data.
Miljödata may have forked out a relatively small amount to the attackers—perhaps because the group saw it as more likely to be paid—but the impact of the hack will be costlier still.
- It may face a fine
- It may face legal action
- Its clients and former clients may face legal consequences
- Those impacted face the pain of compromised personal data
In short, there are a number of actions Miljödata could and should have taken to prevent this mess.

One ransomware-as-a-service, please
Ransomware has been around for decades, but the way it is deployed has shifted dramatically. What used to be crude, scatter-gun spam campaigns are now carefully orchestrated operations run by professional groups. Many operate under a “ransomware-as-a-service” model, renting out their tools and infrastructure to affiliates much like a SaaS company would.
The tactics have evolved, too. Today’s attackers don’t just lock files and demand payment. They also exfiltrate data and threaten to leak it publicly if the ransom isn’t paid. This “double extortion” method ensures that even companies with solid backups are under pressure since they must deal with the data becoming public.
There are even reports of some attackers contacting customers or partners directly to apply additional leverage.
What hasn’t changed is the impact.
Hacks cause operational paralysis, reputational damage, legal consequences and financial loss. The Miljödata case is another unfortunate example that ransomware remains one of the most disruptive threats facing modern organisations.
Why does ransomware hits hardest in supply chains?
One of the most troubling aspects of ransomware today is how often it strikes through the supply chain. Attackers increasingly seek out IT and software vendors that provide services to many organisations. A single breach can cascade into dozens or even hundreds of victims. That means increased potential for a lucrative payout and valuable data.
That’s what makes the Miljödata case so dangerous. Since it provides services to municipalities, universities and corporations across Sweden, the attackers were able to access the data of over a million individuals in one fell swoop.
This “one-to-many” strategy is attractive to attackers because it multiplies their leverage. It also underlines the reality that cybersecurity is a shared responsibility.
Organisations can’t simply outsource risk to suppliers. They must ensure their vendors adhere to the same standards they expect internally. Vendor risk assessments, contractual obligations, and regular audits are no longer optional.
That’s important for all companies, whether your business is a vendor or you work with any third-parties that have data access.
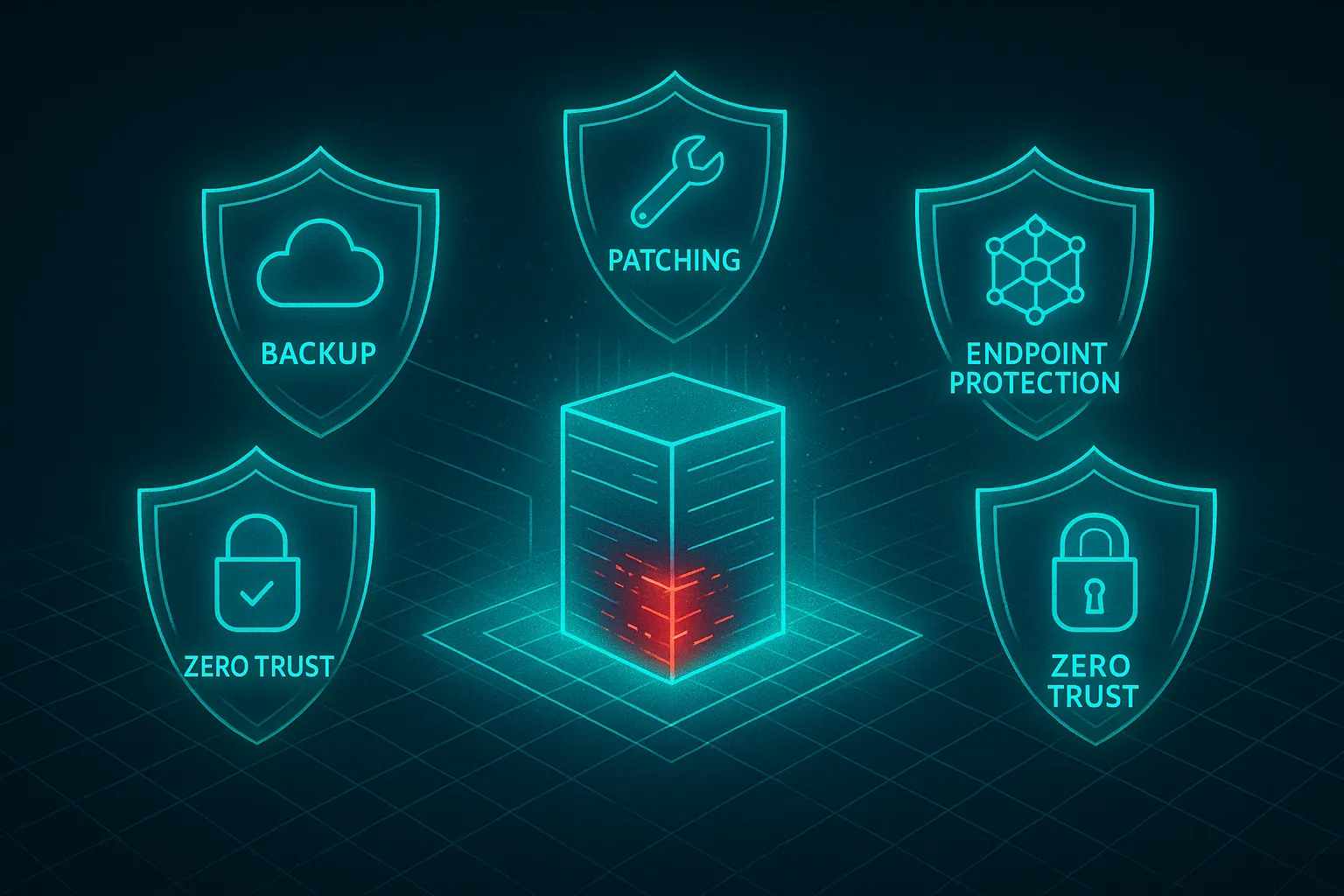
4 core defenses against ransomware
So what can organisations do? The foundation is a set of core defenses that reduce both the likelihood and the impact of ransomware attacks.
1. Backup strategies that actually work
The industry standard remains the 3-2-1 rule: three copies of your data, stored on two different media types, with one copy offsite or offline. Adding immutability, backups that cannot be altered or deleted, even by administrators, further reduces risk.
This is why we emphasise sovereign-cloud and immutable storage in our work at SpaceTime.
2. Patch and update discipline
Ransomware often exploits known vulnerabilities. Many of the worst breaches in history have been enabled by unpatched systems. Creating a strong culture of timely updates across operating systems, applications, firmware and appliances is one of the simplest defenses.
3. Endpoint and network protection
Attackers love lateral movement. Once inside, they quietly explore until they can trigger maximum damage. Multi-layered endpoint security, intrusion detection and continuous monitoring tools can spot suspicious behaviour early, and crucially give defenders time to contain threats.
4. Zero-trust architecture
A zero-trust mindset assumes that no device or user should be automatically trusted. Networks are segmented, access is minimized and strong authentication is enforced. When ransomware does break in, zero trust limits its ability to spread and cause damage.

Not a shocker: Humans remain the weakest link
Technology alone won’t stop ransomware. People remain the first line of defense. Unfortunately, the most common point of failure in these incidents.
It may be hard to believe, but most attacks still begin with a phishing email.
Training staff to recognise suspicious links, attachments or requests is so critical. Training shouldn’t be a once-a-year box-ticking exercise. It must be reinforced through regular phishing simulations and ongoing awareness campaigns.
Equally important is creating a culture where employees feel safe to report mistakes. If someone clicks a bad link, it’s far better they raise the alarm immediately than try to hide it.
Finally, organisations must control insider risk. Role-based access limits the damage if an account is compromised and regular auditing ensures no one retains privileges they don’t need.

Incident response and recovery planning for organisations
The challenge, however, is that even the best defenses can be breached. That’s why every organisation needs a tested incident response plan.
When ransomware strikes, the difference between chaos and controlled recovery comes down to preparation.
A good plan defines:
- Who is on the response team and how to reach them.
- How systems will be isolated to prevent further spread.
- What legal, regulatory, and public-relations steps need to be taken.
- How backups will be restored and operations brought back online.
Tabletop exercises and simulations are invaluable. They reveal gaps in plans and help teams practice under pressure. External partners, including insurers, legal counsel, PR experts and security vendors, should be part of the playbook.
The Miljödata case shows that simply paying the ransom is no guarantee of recovery.
Many organisations that pay up never receive working decryption keys. Even if they do, they’re left with leaked data and potentially significant legal consequences.
Preparation is the only sustainable answer.

Lawsuit incoming! Legal challenges of ransomware
Ransomware is not just a technical crisis; it is also a compliance and legal challenge. Regulations such as the GDPR in Europe impose strict obligations around data protection.
Organisations that lose control of personal data may face fines, investigations and lawsuits. That can apply even if they were not the direct target of an attack, as we may see in the Miljödata case.
Data governance is, therefore, absolutely essential. Companies must know what data they hold, where it resides and how it is protected. They must also conduct regular vendor risk assessments and ensure contracts reflect security requirements.
Cyber insurance can help offset some financial impact, but coverage can vary wildly. Many policies exclude ransom payments or require specific controls to be in place. Understanding those terms in advance is crucial.
The message is clear: compliance isn’t a checkbox. It’s part of the resilience equation.
No need to panic, there are practical steps to take today
If all of this sounds overwhelming, here’s a practical checklist that organisations can act on immediately:
- Audit your ransomware readiness: identify gaps in backups, patching, and monitoring.
- Review your backup strategy: ensure it follows the 3-2-1 rule and includes immutable copies.
- Patch critical systems: prioritize known vulnerabilities that ransomware commonly exploits.
- Run phishing simulations: test and train your employees in real-world conditions.
- Segment your network: reduce the ability for ransomware to spread laterally.
- Test your incident response plan: run a tabletop exercise this quarter.
- Engage external experts: penetration testing and red-team exercises highlight weaknesses before attackers do.
These steps are not particularly revolutionary. It is about discipline and commitment to the overall cause of security.

Conclusion: Vigilance as a continuous practice
The Miljödata breach is a sobering reminder that ransomware has not and is not going away. It remains one of the most profitable and disruptive tools available to cybercriminals.
The lesson is not to live in fear, but to live in preparedness. With layered defenses, trained people, tested recovery plans and strong compliance practices, organisations can weather the storm without catastrophic loss.
At SpaceTime, we believe vigilance is a continuous practice. Ransomware will continue to evolve but so can our defenses. The cost of prevention will always be less than the price of recovery in the long run.
Get in touch with us today to discuss your data storage's preparedness for ransomware.